Privacy, Does it exist?
One can state that privacy, is dead. Or alternatively a form of art that many don’t see the need for much anymore. In society’s world transparency, persona(s), public openness among other things can have beneficial effects, or extensively negative connotations. These connotations can apply to client records, internal communications, and industrial research and development.
Within the media, messages are that government(s) with agencies like the NSA are consistently either breaking encryption, or en mass collecting public data that is available for signals intelligence. To keep in mind, for any culture/civilization there has always been a surveillance system imposed by the state even without the use of what is considered modern technology. Within autocracies/dictatorships the use of dissident reports is essential akin to confessions to the local priest. This results in a compliant relationship between the populous and state.
Ideally within the USA technology companies operates on two levels. One as SaaS (Software as a Service) consumed by the public en masse to which it has no or little privacy guards. (Facebook, Gmail, Instagram, etc.) Within, the industry there are privacy tools such as PGP, encrypted servers, VPN connections among a myriad of other tools that are employed to defend against corporate espionage and eavesdroppers. These tools have been around for 30 years, algorithms are consecutively updated and monitored for penetration testing, when these events occur security keys are changed, as well algorithms are hardened by increasing the bit strength.
CainTech Services LLC operates an encrypted email server point to point. Either via logon to check, and compose emails, additionally while being stored on the server itself. Encryption updates are applied monthly to keep data confidential and secure. The use of PGP, RSA, and Diffie-Hellman key exchange along with forward secrecy. In terms of forward secrecy new encrypted keys are randomly generated for each session.
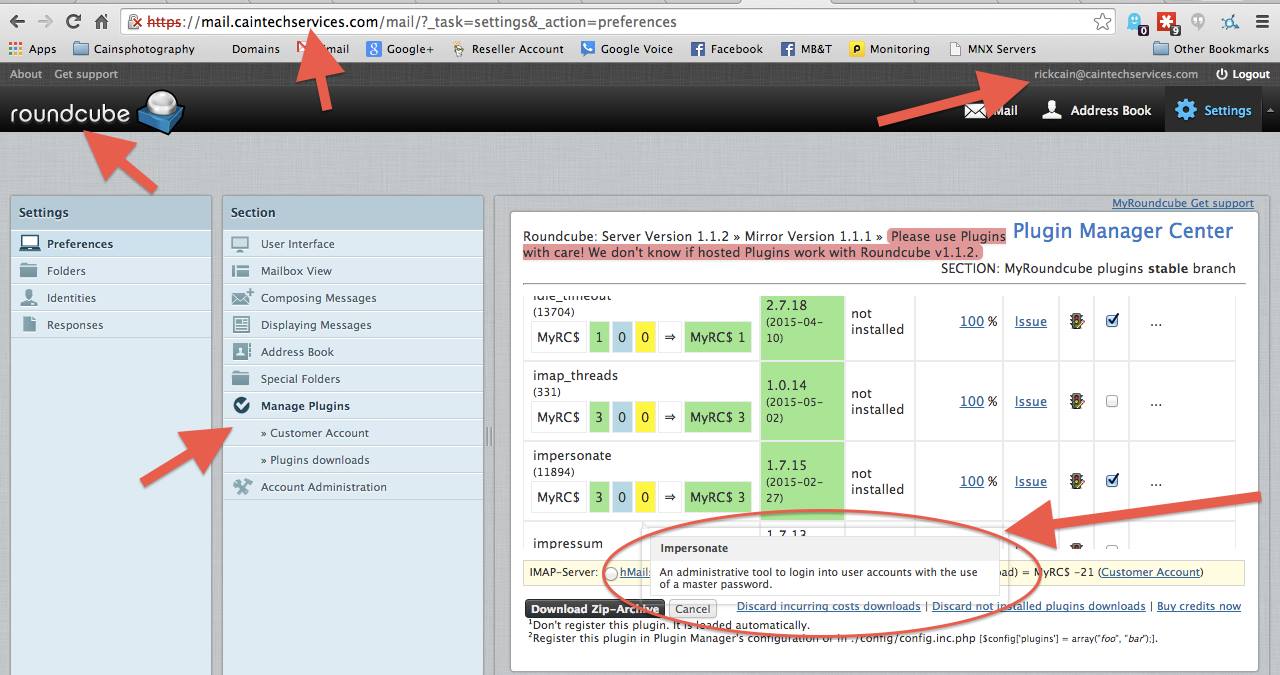
What makes CainTech Services different is a layer of transparency to our users. An example being our disclosure to our clientele
The accountability of this disclosure is paramount as well should be seen as a Public Service Announcement. If CainTech Services, as a service provider can impersonate said user via a master password. It creates a system that is inherently insecure.
For the record, this feature will NEVER be in-use on our servers.
Remember this, if CainTech Services is capable of impersonating our clientele. What is Yahoo, Google, Hotmail and other services capable of.


Leave a Reply